Cisco Ios Version
On any Cisco network component, the show version command is applicable to any of the hardware using Cisco Internetwork Operating System (IOS), including switches. The show version command displays slightly different information depending on the type of device you use it on. Look at the output of the.
| Developer | Cisco Systems |
|---|---|
| Working state | Current |
| Source model | Closed source |
| Latest release | 15.8(3)M[1] / January 22, 2019; 7 months ago |
| Available in | English |
| Platforms | The majority of Cisco routers and current Cisco switches |
| Default user interface | Command line interface |
| Official website | Cisco IOS |
- Securing Cisco An objective, consensus-driven security guideline for the Cisco Network Devices. An objective, consensus-driven security guideline for the Cisco Network Devices. A step-by-step checklist to secure Cisco: For Cisco Firewall 9.5 (CIS Cisco Firewall Benchmark version 4.1.0).
- As of 2018, two versions of iOS were never released. IPhone OS 1.2, which after the first beta was replaced by a 2.0 version number; the second beta was named 2.0 beta 2 instead of 1.2 beta 2. The other was iOS 4.2, replaced with 4.2.1 due to a Wi-Fi bug in 4.2 beta 3, causing Apple to release 2 golden masters (4.2 GM and 4.2.1 GM).
- XML Examples for the Cisco ASA Device Package Software, Version 1.3(10) for ACI 05/Feb/2018 Release Notes for the Cisco ASA Device Package Software, Version 1.2(11) for ACI 02/Nov/2018 Release Notes for the Cisco ASA Device Package Software, Version 1.2(10) for ACI 02/Mar/2018.
Cisco Internetwork Operating System (IOS) is a family of network operating systems used on many Cisco Systemsrouters and current Cisco network switches. Earlier, Cisco switches ran CatOS. IOS is a package of routing, switching, internetworking and telecommunications functions integrated into a multitasking operating system. Although the IOS code base includes a cooperative multitasking kernel, most IOS features have been ported to other kernels such as QNX and Linux for use in Cisco products.
Not all Cisco products run IOS. Notable exceptions include ASA security products, which run a Linux-derived operating system, carrier routers which run IOS-XR and Cisco's Nexus switch and FC switch products which run Cisco NX-OS.
- 7Versioning
- 7.1Trains
History[edit]
The IOS network operating system was developed in the 1980s for routers that had only 256 kB memory and low CPU processing power. Through modular extensions IOS has been adapted to increasing hardware capabilities and new networking protocols.[2] When IOS was developed, Cisco Systems' main product line were routers. The company acquired a number of young companies that focused on network switches, such as the inventor of the first Ethernet switch Kalpana, and as a result Cisco switches did not run the IOS. The Cisco Catalyst series would for some time run the CatOS.[3] In early modular chassis network switches from Cisco, modules with layer 3 routing functionalities were separate devices that ran IOS, while the layer 2 switch modules ran CatOS. Cisco eventually introduced the native mode for chassis, so that they only run one operating system.[specify] For the Nexus switches Cisco developed NX-OS, which is similar to IOS,[4] except that it is Linux-based.[5]
Command-line interface[edit]
The IOS command-line interface (CLI) provides a fixed set of multiple-word commands. The set available is determined by the 'mode' and the privilege level of the current user. 'Global configuration mode' provides commands to change the system's configuration, and 'interface configuration mode' provides commands to change the configuration of a specific interface. All commands are assigned a privilege level, from 0 to 15, and can only be accessed by users with the necessary privilege. Through the CLI, the commands available to each privilege level can be defined.
Most builds of IOS include a Tcl interpreter. Using the embedded event manager feature, the interpreter can be scripted to react to events within the networking environment, such as interface failure or periodic timers.
Available command modes include:[6]
- User EXEC Mode
- Privileged EXEC Mode
- Global Configuration Mode
- ROM Monitor Mode
- Setup Mode
- More than 100 configuration modes and submodes.
Architecture[edit]
Cisco IOS has a monolithic architecture, owing to the limited hardware resources of routers and switches in the 1980s. This means that all processes have direct hardware access to conserve CPU processing time. There is no memory protection between processes and IOS has a run to completion scheduler, which means that the kernel does not pre-empt a running process. Instead the process must make a kernel call before other processes get a chance to run. IOS considers each process a single thread and assigns it a priority value, so that high priority processes are executed on the CPU before queued low priority processes, but high priority processes can not interrupt running low priority processes.[7]
The Cisco IOS monolithic kernel does not implement memory protection for the data of different processes. The entire physical memory is mapped into one virtual address space. The Cisco IOS kernel does not perform any memory paging or swapping. Therefore the addressable memory is limited to the physical memory of the network device on which the operating system is installed. IOS does however support aliasing of duplicated virtual memory contents to the same physical memory. This architecture was implemented by Cisco in order to ensure system performance and minimize the operational overheads of the operating system.[8]
The disadvantage of the IOS architecture is that it increases the complexity of the operating system, data corruption is possible as one process can write over the data of another, and one process can destabilize the entire operating system or even cause a software-forced crash. In the event of an IOS crash, the operating system automatically reboots and reloads the saved configuration.[9]
Routing[edit]
In all versions of Cisco IOS, packet routing and forwarding (switching) are distinct functions. Routing and other protocols run as Cisco IOS processes and contribute to the Routing Information Base (RIB). This is processed to generate the final IP forwarding table (FIB, Forwarding Information Base), which is used by the forwarding function of the router. On router platforms with software-only forwarding (e.g., Cisco 7200), most traffic handling, including access control list filtering and forwarding, is done at interrupt level using Cisco Express Forwarding (CEF) or dCEF (Distributed CEF). This means IOS does not have to do a process context switch to forward a packet. Routing functions such as OSPF or BGP run at the process level. In routers with hardware-based forwarding, such as the Cisco 12000 series, IOS computes the FIB in software and loads it into the forwarding hardware (such as an ASIC or network processor), which performs the actual packet forwarding function.
Interface descriptor block[edit]
An Interface Descriptor Block, or simply IDB, is a portion of memory or Cisco IOS internal data structure that contains information such as the IP address, interface state, and packet statistics for networking data. Cisco's IOS software maintains one IDB for each hardware interface in a particular Cisco switch or router and one IDB for each subinterface. The number of IDBs present in a system varies with the Cisco hardware platform type.
Packages and feature sets[edit]
IOS is shipped as a unique file that have been compiled for specific Cisco network devices. Each IOS Image therefore include a feature set, which determine the command-line interface (CLI) commands and features that are available on different Cisco devices. Upgrading to another feature set therefore entails the installation of a new IOS image on the networking device and reloading the IOS operating system. Information about the IOS version and feature-set running on a Cisco device can be obtained with the show version command.[10]
Most Cisco products that run IOS also have one or more 'feature sets' or 'packages', typically eight packages for Cisco routers and five packages for Cisco network switches. For example, Cisco IOS releases meant for use on Catalyst switches are available as 'standard' versions (providing only basic IP routing), 'enhanced' versions, which provide full IPv4 routing support, and 'advanced IP services' versions, which provide the enhanced features as well as IPv6 support.[11]
Beginning with the 1900, 2900 and 3900 series of ISR Routers, Cisco revised the licensing model of IOS.[citation needed] To simplify the process of enlarging the feature-set and reduce the need for network operating system reloads, Cisco introduced universal IOS images, that include all features available for a device and customers may unlock certain features by purchasing an additional software license.[12] The exact feature set required for a particular function can be determined using the Cisco Feature Set Browser. Routers come with IP Base installed, and additional feature pack licenses can be installed as bolt-on additions to expand the feature set of the device. The available feature packs are:
- Data adds features like BFD, IP SLAs, IPX, L2TPv3, Mobile IP, MPLS, SCTP.
- Security adds features like VPN, Firewall, IP SLAs, NAC.
- Unified Comms adds features like CallManager Express, Gatekeeper, H.323, IP SLAs, MGCP, SIP, VoIP, CUBE(SBC).
ISO images can not be updated with software bug fixes. To patch a vulnerability in an IOS a binary file with the entire operating system needs to be loaded.[13]
Versioning[edit]
Cisco IOS is versioned using three numbers and some letters, in the general form a.b(c.d)e, where:
- a is the major version number.
- b is the minor version number.
- c is the release number, which begins at one and increments as new releases in a same way a.b train are released.[clarification needed] 'Train' is Cisco-speak for 'a vehicle for delivering Cisco software to a specific set of platforms and features.'
- d (omitted from general releases) is the interim build number.
- e (zero, one or two letters) is the software release train identifier, such as none (which designates the mainline, see below), T (for Technology), E (for Enterprise), S (for Service provider), XA as a special functionality train, XB as a different special functionality train, etc.
Rebuilds – Often a rebuild is compiled to fix a single specific problem or vulnerability for a given IOS version. For example, 12.1(8)E14 is a Rebuild, the 14 denoting the 14th rebuild of 12.1(8)E. Rebuilds are produced to either quickly repair a defect, or to satisfy customers who do not want to upgrade to a later major revision because they may be running critical infrastructure on their devices, and hence prefer to minimize change and risk.
Interim releases – Are usually produced on a weekly basis, and form a roll-up of current development effort. The Cisco advisory web site may list more than one possible interim to fix an associated issue (the reason for this is unknown to the general public).
Maintenance releases – Rigorously tested releases that are made available and include enhancements and bug fixes. Cisco recommend upgrading to Maintenance releases where possible, over Interim and Rebuild releases.
Trains[edit]
Cisco says, 'A train is a vehicle for delivering Cisco software to a specific set of platforms and features.'[11]
Until 12.4[edit]
Before Cisco IOS release 15, releases were split into several trains, each containing a different set of features. Trains more or less map onto distinct markets or groups of customers that Cisco targeted.[11]

- The mainline train is intended to be the most stable release the company can offer, and its feature set never expands during its lifetime. Updates are released only to address bugs in the product. The previous technology train becomes the source for the current mainline train — for example, the 12.1T train becomes the basis for the 12.2 mainline. Therefore, to determine the features available in a particular mainline release, look at the previous T train release. [14]:6
- The T – Technology train, gets new features and bug fixes throughout its life, and is therefore potentially less stable than the mainline. (In releases prior to Cisco IOS Release 12.0, the P train served as the Technology train.) Cisco doesn't recommend usage of T train in production environments unless there is urgency to implement a certain T train's new IOS feature. [14]:6
- The S – Service Provider train, runs only on the company's core router products and is heavily customized for Service Provider customers. [14]:6
- The E – Enterprise train, is customized for implementation in enterprise environments. [14]:6
- The B – broadband train, supports internet based broadband features. [14]:6
- The X* (XA, XB, etc.) – Special Release train, contains one-off releases designed to fix a certain bug or provide a new feature. These are eventually merged with one the above trains. [14]:15
There were other trains from time to time, designed for specific needs — for example, the 12.0AA train contained new code required for Cisco's AS5800 product.
Since 15.0[edit]
Starting with Cisco IOS release 15, there is just a single train, the M/T train. This train includes both extended maintenance releases and standard maintenance releases. The M releases are extended maintenance releases, and Cisco will provide bug fixes for 44 months. The T releases are standard maintenance releases, and Cisco will only provide bug fixes for 18 months.
Security and vulnerabilities[edit]
Because IOS needs to know the cleartext password for certain uses, (e.g., CHAP authentication) passwords entered into the CLI by default are weakly encrypted as 'Type 7' ciphertext, such as 'Router(config)#username jdoe password 7 0832585B1910010713181F'. This is designed to prevent 'shoulder-surfing' attacks when viewing router configurations and is not secure – they are easily decrypted using software called 'getpass' available since 1995, or 'ios7crypt',[15] a modern variant, although the passwords can be decoded by the router using the 'key chain' command and entering the type 7 password as the key, and then issuing a 'show key' command; the above example decrypts to 'stupidpass'.[16] However, the program will not decrypt 'Type 5' passwords or passwords set with the enable secret command, which uses saltedMD5 hashes.[17]
Cisco recommends that all Cisco IOS devices implement the authentication, authorization, and accounting (AAA) security model. AAA can use local, RADIUS, and TACACS+ databases. However, a local account is usually still required for emergency situations.[18]
At the Black Hat Briefings conference in July 2005, Michael Lynn, working for Internet Security Systems at the time, presented information about a vulnerability in IOS.[19]Cisco had already issued a patch, but asked that the flaw not be disclosed.[20]Cisco filed a lawsuit, but settled after an injunction was issued to prevent further disclosures.[21]
16,851 Downloads Submitted Nov 23, 2004 by SurleyBlaine (DG Member):' ScanGear CS 7.0 for Windows is - A 32-bit TWAIN-compliant scanner driver for Canon CanoScan LiDE 20/N670U/N676U and CanoScan LiDE 30/N1240U scanners. Popular Driver Updates for Canon CanoScan LiDE 100 Ad Supported OS: Windows 10, Windows 8.1, Windows 7, Windows Vista, Windows XPFile Version: Version 3.8.0File Size: 269 KBFile Name:Overall Rating. Install canoscan lide 100 software download.
IOS XR train[edit]
For Cisco products that required very high availability, such as the Cisco CRS-1, the limitations of a monolithic kernel were not acceptable. In addition, competitive router operating systems that emerged 10–20 years after IOS, such as Juniper's JUNOS, were designed not to have these limitations.[22] Cisco's response was to develop a tree of the Cisco IOS that offered modularity and memory protection between processes, lightweight threads, pre-emptive scheduling and the ability to independently restart failed processes. The IOS XR development train used the real-time operating systemmicrokernel (QNX), so a large part of the IOS source code was re-written to take advantage of the features offered by the kernel. In 2005 Cisco introduced the Cisco IOS XR network operating system on the 12000 series of network routers, extending the microkernel architecture from the CRS-1 routers to Cisco's widely deployed core routers. In 2006 Cisco introduced IOS Software Modularity, which extends the microkernel architecture into the IOS environment, while still providing the software upgrade capabilities. IOS XR was subsequently made available on the Catalyst 6500 enterprise switches.[citation needed]
See also[edit]
References[edit]
- ^'Cross Platform Release Notes for Cisco IOS Release 15.8(3)M'. January 22, 2019. Retrieved March 30, 2019.
- ^Brad Edgeworth, Aaron Foss & Ramiro Garza Rios (2014). IP Routing on Cisco IOS, IOS XE, and IOS XR: An Essential Guide to Understanding and Implementing IP Routing Protocols. Cisco Press. p. 2. ISBN9780133846768.CS1 maint: uses authors parameter (link)
- ^Gary A. Donahue (2011). Network Warrior: Everything You Need to Know That Wasn't on the CCNA Exam. O'Reilly Media. p. 10. ISBN9781449309350.
- ^Gary A. Donahue (2011). Network Warrior: Everything You Need to Know That Wasn't on the CCNA Exam. O'Reilly Media. p. 222. ISBN9781449309350.
- ^Gary A. Donahue (2011). Network Warrior: Everything You Need to Know That Wasn't on the CCNA Exam. O'Reilly Media. p. 274. ISBN9781449309350.
- ^'Cisco IOS Command Modes'. Cisco. Retrieved 27 September 2015.
- ^Brad Edgeworth, Aaron Foss & Ramiro Garza Rios (2014). IP Routing on Cisco IOS, IOS XE, and IOS XR: An Essential Guide to Understanding and Implementing IP Routing Protocols. Cisco Press. p. 2. ISBN9780133846768.CS1 maint: uses authors parameter (link)
- ^Brad Edgeworth, Aaron Foss & Ramiro Garza Rios (2014). IP Routing on Cisco IOS, IOS XE, and IOS XR: An Essential Guide to Understanding and Implementing IP Routing Protocols. Cisco Press. p. 2. ISBN9780133846768.CS1 maint: uses authors parameter (link)
- ^Brad Edgeworth, Aaron Foss & Ramiro Garza Rios (2014). IP Routing on Cisco IOS, IOS XE, and IOS XR: An Essential Guide to Understanding and Implementing IP Routing Protocols. Cisco Press. p. 2. ISBN9780133846768.CS1 maint: uses authors parameter (link)
- ^Brad Edgeworth, Aaron Foss & Ramiro Garza Rios (2014). IP Routing on Cisco IOS, IOS XE, and IOS XR: An Essential Guide to Understanding and Implementing IP Routing Protocols. Cisco Press. p. 2. ISBN9780133846768.CS1 maint: uses authors parameter (link)
- ^ abc'Cisco IOS and NX-OS Software Reference Guide', Cisco White Paper, retrieved June 18, 2013
- ^Brad Edgeworth, Aaron Foss & Ramiro Garza Rios (2014). IP Routing on Cisco IOS, IOS XE, and IOS XR: An Essential Guide to Understanding and Implementing IP Routing Protocols. Cisco Press. p. 3. ISBN9780133846768.CS1 maint: uses authors parameter (link)
- ^Brad Edgeworth, Aaron Foss & Ramiro Garza Rios (2014). IP Routing on Cisco IOS, IOS XE, and IOS XR: An Essential Guide to Understanding and Implementing IP Routing Protocols. Cisco Press. p. 4. ISBN9780133846768.CS1 maint: uses authors parameter (link)
- ^ abcdefRullan, John (2005), 'Understanding Cisco IOS Naming Conventions'(PDF), Cisco Academy Conference Presentation, retrieved October 10, 2016
- ^ios7crypt
- ^Insecure.org Cisco password decryption
- ^'Cisco IOS Password Encryption Facts'. Retrieved 12 Sep 2017.
- ^'Cisco 500-052 Test'. Retrieved 21 Feb 2017.
- ^Kim Zetter (August 1, 2005). 'Router Flaw Is a Ticking Bomb'. Wired. Retrieved August 9, 2014.
- ^Kim Zetter (July 27, 2005). 'Cisco Security Hole a Whopper'. Wired. Retrieved August 9, 2014.
- ^'Statement on Federal District Court Injunction (Black Hat Presentation)'. Press release. Cisco Systems. July 28, 2005. Archived from the original on February 5, 2012. Retrieved June 18, 2013.
- ^Juniper Networks: JunOS
External links[edit]
Becoming proficient with the Cisco IOS means learning some essential commands. This quick reference describes 10 commands you'll need to rely on when handling various configuration and troubleshooting tasks.
#1: The '?'
It may seem entirely too obvious that you should know how to type ? to ask for help when using the Cisco IOS. However, the Cisco IOS is completely different from other operating systems when it comes to using the question mark (help key). As the IOS is a command-line operating system with thousands of possible commands and parameters, using the ? can save your day.
You can use the command in many ways. First, use it when you don't know what command to type. For example, type ? at the command line for a list of all possible commands. You can also use ? when you don't know what a command's next parameter should be. For example, you might type show ip ? If the router requires no other parameters for the command, the router will offer <CR> as the only option.
Finally, use ? to see all commands that start with a particular letter. For example, show c? will return a list of commands that start with the letter 'c'.
#2: show running-configuration
The show running-config command shows the router, switch, or firewall's current configuration. The running-configuration is the config that is in the router's memory. You change this config when you make changes to the router. Keep in mind that config is not saved until you do a copy running-configuration startup-configuration. This command can be abbreviated sh run.
Other web browsers such as Internet Explorer are not affected. Tor browser bundle download for android. It can run off a USB flash drive, comes with a pre-configured web browser called Aurora, and is self-contained.Only web pages visited through the included Firefox browser will be sent via Tor. Make sure that it says 'Tor Enabled' in the bottom right corner before using it.
SEE: Server deployment/migration checklist (Tech Pro Research)
#3: copy running-configuration startup-configuration
This command will save the configuration that is currently being modified (in RAM), also known as the running-configuration, to the nonvolatile RAM (NVRAM). If the power is lost, the NVRAM will preserve this configuration. In other words, if you edit the router's configuration, don't use this command and reboot the router—those changes will be lost. This command can be abbreviated copy run start. The copy command can also be used to copy the running or startup configuration from the router to a TFTP server in case something happens to the router.
#4: show interface
The show interface command displays the status of the router's interfaces. Among other things, this output provides the following:
- Interface status (up/down)
- Protocol status on the interface
- Utilization
- Errors
- MTU
This command is essential for troubleshooting a router or switch. It can also be used by specifying a certain interface, like sh int g0/0.
#5: show ip interface
More about Networking
Even more popular than show interface are show ip interface and show ip interface brief. The show ip interface command provides tons of useful information about the configuration and status of the IP protocol and its services, on all interfaces. The show ip interface brief command provides a quick status of the interfaces on the router, including their IP address, Layer 2 status, and Layer 3 status.
#6: config terminal, enable, interface, and router
Cisco routers have different modes where only certain things can be shown or certain things can be changed. Being able to move between these modes is critical to successfully configuring the router.
For example, when logging in, you start off at the user mode (where the prompt looks like >). From there, you type enable to move to privileged mode (where the prompt looks like #). In privileged mode, you can show anything but not make changes. Next, type config terminal (or config t) to go to global configuration mode (where the prompt looks like router(config)# ). From here, you can change global parameters. To change a parameter on an interface (like the IP address), go to interface configuration mode with the interface command (where the prompt looks like router(config-if)#). Also from the global configuration mode, you can go into router configuration using the router {protocol} command. To exit from a mode, type exit.
#7: no shutdown
The no shutdown command enables an interface (brings it up). This command must be used in interface configuration mode. It is useful for new interfaces and for troubleshooting. When you're having trouble with an interface, you may want to try a shut and no shut. Of course, to bring the interface down, reverse the command and just say shutdown. This command can be abbreviated no shut.
SEE: Systems downtime expense calculator (Tech Pro Research)
#8: show ip route
The show ip route command is used to show the router's routing table. This is the list of all networks that the router can reach, their metric (the router's preference for them), and how to get there. This command can be abbreviated sh ip ro and can have parameters after it, like sh ip ro ospf for all OSPF routes. To clear the routing table of all routes, you do clear ip route. To clear it of just one routes, issue the command clear ip route x.x.x.x (where x.x.x.x is the network you want to clear).
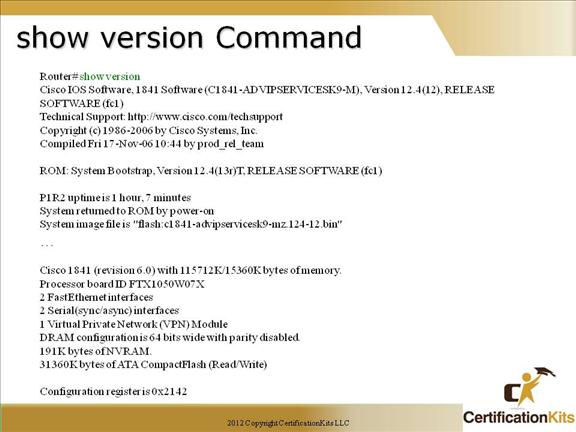
#9: show version
The show version command gives you the router's configuration register (essentially, the router's firmware settings for booting up), the last time the router was booted, the version of the IOS, the name of the IOS file, the model of the router, and the router's amount of RAM and Flash. This command can be abbreviated sh ver.
#10: debug
The debug command has many options and does not work by itself. It provides detailed debugging output on a certain application, protocol, or service. For example, debug ip routing will tell you every time a route is added to or removed from the router. Debugging can be dangerous as its process takes priority over all others. Be prepared to disable the feature using the no debug command or undebug all command.
Latest Cisco Ios
Editors note: This article was originally published on TechRepublic July 25, 2006. It was updated on November 30, 2017. The original version is also available as a PDF download.
Data Center Trends Newsletter
DevOps, virtualization, the hybrid cloud, storage, and operational efficiency are just some of the data center topics we'll highlight. Delivered Mondays and Wednesdays
Sign up today Sign up todayAlso see
Cisco Ios Version 12.2 Vulnerabilities
- Which Cisco certifications will be in demand in 2017? (TechRepublic)
- Download: Network security policy (Tech Pro Research)
- Cisco: Most IoT projects are failing due to lack of experience and security (ZDNet)
- Cisco's new predictive services aim to fill the tech skills gap with AI (TechRepublic)
- Cisco Live 2017: Artificial intelligence and machine learning will herald in the next era of networking (TechRepublic)